Digital Security at the University Now – digital security review 4/2025

Digital Security at the University Now is a review of topical matters related to information security and digital security at the University. The review is published four times a year in Flamma and the Studies Service. We will include a selection of topical matters from the National Cyber Security Centre’s publications as well as the University’s digital security news.
On this review:
- News from the National Cyber Security Centre
- New types of scams: AitM attacks
- Did you miss the Digital Security at the University webinar earlier in the autumn?
- The Korkeakoulujen tietoturvaajat podcast is back soon with new episodes
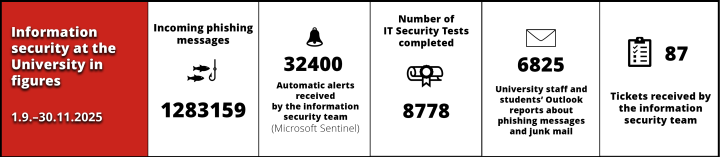
1. News from the National Cyber Security Centre
In this section, we gather topical content from the latest publications and reviews of the National Cyber Security Centre.
- Stay alert for parcel delivery scams! Fraud increases as the Christmas season approach Read more about the parcel delivery scams and other recently reported scams on the National Cyber Security Centre’s weekly review
- See other news from the National Cyber Security Centre on the National Cyber Security Centre website under Information Security now.
2. New types of scams: AitM attacks
As protection methods develop, scamming methods also adapt to bypass the new and more comprehensive protection methods. A new type of scam that is rapidly becoming more prevalent is AitM, or “Adversary-in-the-Middle” attacks.
What is AitM phishing, and how does it differ from more traditional phishing?
As we are used to seeing with phishing messages, AitM attacks are also based on a sense of urgency and putting pressure on the recipient to make hasty decisions. A special feature of AitM attacks is the use of previously hijacked usernames. The hijacked usernames are used to send a phishing message from an email address known to the new victim. This makes the scam message more difficult to identify. If a person or service you know sends a message to you that feels off to you, you can check the authenticity of the message by contacting the person by some means other than e-mail, such as by calling them.
Like a traditional phishing message, an AitM attack email typically contains a link to a phishing site that mimics a genuine login page. Phishing websites often look very authentic, which can make it particularly difficult to recognise the fake website at a glance. Often, the address of the link to the website is the only way to detect phishing. Therefore, please always check the links in the messages you receive to make sure that their addresses look correct and, if you are not sure, do not click them.
If you use the link in the AitM attack message to access a phishing site and enter your information there, the information will immediately be forwarded through the criminal’s servers to the actual login portal. In the same situation, the victim will be asked to enter their multi-factor authentication information in the correct portal. After a successful login, the criminals can access the resources and applications of the victim’s Microsoft365 account. So, the AitM attack differs from more traditional phishing in that the attacker uses technical methods, such as session hijacking, to gain access to the data. This way, it is possible to bypass traditional security measures, such as multi-factor authentication.
How are the hijacked Microsoft365 user accounts used?
Criminals are usually particularly interested in any invoices and confidential information in the victim’s e-mail. If the account is used to process invoices or money transactions, the criminals can use the hijacked e-mail account for invoicing fraud, for example.
The hijacked accounts may also be bought and sold on criminal forums and used as part of new attacks, as described above. Critical and sensitive information on e-mail accounts may also be leaked, stolen or sold on. With redirection rules, criminals can potentially redirect e-mail traffic from the hijacked account to another address, which makes it possible to track and read e-mail traffic without the victim noticing.
Summary:
- Be careful with links in messages or their attachments.
- If a message from a person or service you know feels off to you, you can check the authenticity of the message by contacting them by some means other than e-mail, such as by calling.
- For more information on AiTM attacks and how to defend against them, please visit the websites of the National Cyber Security Centre or Microsoft.
3. Did you miss the Digital Security at the University webinar earlier in the autumn?
See the recording and event materials on the information security pages in Flamma.
The webinar is spoken in finnish, but the webinar materials on Howspace can be translated with the help of a translater tool (small globe icon) in the upper right corner of the Howspace page.
4. The Korkeakoulujen tietoturvaajat podcast is soon back with new episodes
Korkeakoulun tietoturvaajat is a podcast about information security at higher education institutions (in finnish). More episodes have now been recorded, and new content will be published shortly after the turn of the year.
You can listen to the previous episodes on Spotify or Soundcloud (only in finnish).